CertExams.com released a thorough update to their flagship software, Network Simulator with Designer for CCNA® , to include functionality for the following:
- Site to Site VPN configuration between routers
- FHRP configuration
VPN (Virtual Private Network) is widely used these days for security and confidentiality of communication between hosts. The two main types of VPN are Site-to-site VPN and Remote-to-Site VPN. In Site-to-site VPN, a secure tunnel is formed between two peers within the communication channel. An example configuration scenario is shown in the figure below:
 Photo Courtesy: Brocade.com, a leading networking equipment manufacturer.
Photo Courtesy: Brocade.com, a leading networking equipment manufacturer.
As may seen in the exhibit, the VPN is configured between two routers. A site-to-site VPN is also called router-to-router VPN. The hosts on LAN are unaware of the VPN between routers V1 and V2. However, all the communication between routers V1 and V2 moves securely over OpenVPN tunnel. You typically need a NAT (Network Address Translation) to translate internal IP address 192.168.200.1 to external IP address 12.34.56.78 and vice versa (for incoming traffic). The same thing is done at router V2 also. The word “tunnel” may be a bit misleading some times. Note that there is no route and bandwidth allocated between the routers when a tunnel is formed. A VPN typically secures the communication channel but not the route or bandwidth. A VPN connections use 1) Encapsulation 2) Authentication, and 3) Data encryption.
In Encapsulation, user data (i.e. TCP/IP packets) is wrapped around by using encapsulation protocol such as GRE, IPsec, L2F, PPTP, or L2TP. The encapsulated data packets are again wrapped inside carrier protocol packet, and then routed across the public network.
For site-to-site VPNs, the encapsulating protocol is usually IPsec or GRE (Generic Routing Encapsulation). For remote-access VPNs, tunneling normally takes place using PPP (Point-to-Point Protocol). PPP tunneling will use one of PPTP, L2TP or L2F.
When using site-to-site VPN, any user can access remote site from any of the computers inside the firewall (local network). For this purpose, one needs to configure AAA (Authentication, Authorization, and Accounting), so that one needs to authenticate to access any resources at the other end of the VPN tunnel to restrict user access.
Remote access VPN is typically used with home and mobile users to connect to the corporate office. For example, a mobile traveler can connect to the Corporate head quarters using his laptop computer securely using a public Wi-Fi connection. Please see the figure below:
 Photo courtesy: brocade.com, a leading networking equipment manufacturer.
Photo courtesy: brocade.com, a leading networking equipment manufacturer.
As seen in the figure, a remote user communicates with the sever securely over VPN tunnel. All the user information, login credentials, etc. are encrypted when using VPN tunnel. In remote access VPN, usually, a client is installed on the remote user’s computer. Alternatively, the remote user uses SSL enabled browser session to communicate with the corporate network (shown as Private Network in the figure)
FHRP (First Hop Redundancy Protocol): Usually, when a subscriber connects to an ISP using Wi-Fi router, he will have single point of failure. i.e. if the router fails, the connection to the Internet fails. FHRP allows redundancy or a fail over mechanism, thus ensuring that there is no single point of failure for a subscriber to the Internet. There are several protocol defined for FHRP, popular among these are: HSRP, VRRP, and GLBP.
HSRP, short for Hot Standby Router Protocol, is a Cisco proprietary protocol, and supported by most of the Cisco routers.
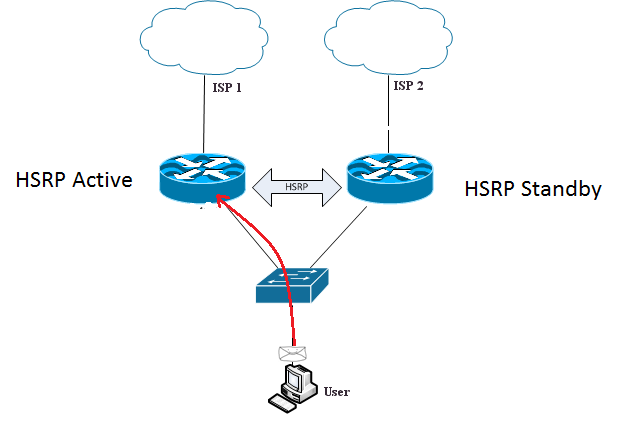 A simple HSRP configuration is shown in the figure. In HSRP, one router acts as an Active router and the other as Standby router. There can be more than two routers in HSRP configuration, however, only one router is put in Standby state using a selection criteria. HSRP routers may be assigned “Priority” so that a network admin can choose which router has be in HSRP Active state and which has to be in Standby state.
A simple HSRP configuration is shown in the figure. In HSRP, one router acts as an Active router and the other as Standby router. There can be more than two routers in HSRP configuration, however, only one router is put in Standby state using a selection criteria. HSRP routers may be assigned “Priority” so that a network admin can choose which router has be in HSRP Active state and which has to be in Standby state.
VRRP, short for Virtual Router Redundancy Protocol, is a standards based protocol. It is quite similar to HSRP in configuration and functionality.
GLBP, short for Gateway Load Balancing Protocol, is slightly advanced, in the sense, that it supports load balancing by default. Otherwise, it is similar to other two redundancy protocols.
CertExams.com CCNA Netsim, offers a virtual networking environment, where in, one can create a network with Cisco(R) routers, switches, and other networking elements and experiment. The software has a GUI based designer that allows drag-n-drop functionality for designing one’s own network. Several labs on HSRP, and site-to-site VPN have been added for hands-on practice. The software is intended for learning purpose with limited set of commands support.
List of available CCNA labs may be viewed by going to the product page. You may download the free demo version of the software by going to the product download page.
Disclaimer: CertExams.com is not associated nor affiliated with Cisco Systems, or Brocade. Cisco®, CCNA® are registered trademarks of Cisco Systems, and Brocade® is trademark of Brocade/Broadcom Limited and duly recognized.